#Network Encryption Size
Explore tagged Tumblr posts
Text
Network Encryption Share | Segmented by Top Manufacturers & Geography Regions

Network Encryption Market Information
The Network Encryption Market Report provides essential insights for business strategists, offering a comprehensive overview of industry trends and growth projections. It includes detailed historical and future data on costs, revenues, supply, and demand, where applicable. The report features an in-depth analysis of the value chain and distributor networks.
Employing various analytical techniques such as SWOT analysis, Porter’s Five Forces analysis, and feasibility studies, the report offers a thorough understanding of competitive dynamics, the risk of substitutes and new entrants, and identifies strengths, challenges, and business opportunities. This detailed assessment covers current patterns, driving factors, limitations, emerging developments, and high-growth areas, aiding stakeholders in making informed strategic decisions based on both current and future market trends. Additionally, the report includes an examination of the Automatic Rising Arm Barriers sector and its key opportunities.
According to Straits Research, the global Network Encryption market size was valued at USD 4 Billion in 2021. It is projected to reach from USD XX Billion in 2022 to USD 8 Billion by 2030, growing at a CAGR of 9% during the forecast period (2022–2030).
Get Free Request Sample Report @ https://straitsresearch.com/report/network-encryption-market/request-sample
TOP Key Industry Players of the Network Encryption Market
Thales Trusted Cyber Technologies
ATMedia Gmbh
Atos SE
Juniper Networks Inc.
Certes Networks Inc.
Senetas Corporation Ltd
Viasat Inc.
Raytheon Technologies Corporation
Securosys SA
Packetlight Networks
Rohde & Schwarz Cybersecurity GmbH
Global Network Encryption Market: Segmentation
As a result of the Network Encryption market segmentation, the market is divided into sub-segments based on product type, application, as well as regional and country-level forecasts.
By Solution
Network Encryption Platforms
On-Premise
Cloud-based
Network Encryption Devices
Services
Professional Services
Security Consulting
Training & Education
Support & Maintenance
Managed Services
By Deployment Type
Cloud
On-premises
By Component
Hardware
Solutions and Services
By Organization Size
Small and Medium-sized Enterprises
Large-sized Enterprises
By End-User Industry
Telecom and IT
BFSI
Government
Media and Entertainment
Healthcare
Retail & E-Commerce
Other End-user Industries
Browse Full Report and TOC @ https://straitsresearch.com/report/network-encryption-market/request-sample
Reasons for Buying This Report:
Provides an analysis of the evolving competitive landscape of the Automatic Rising Arm Barriers market.
Offers analytical insights and strategic planning guidance to support informed business decisions.
Highlights key market dynamics, including drivers, restraints, emerging trends, developments, and opportunities.
Includes market estimates by region and profiles of various industry stakeholders.
Aids in understanding critical market segments.
Delivers extensive data on trends that could impact market growth.
Research Methodology:
Utilizes a robust methodology involving data triangulation with top-down and bottom-up approaches.
Validates market estimates through primary research with key stakeholders.
Estimates market size and forecasts for different segments at global, regional, and country levels using reliable published sources and stakeholder interviews.
About Straits Research
Straits Research is dedicated to providing businesses with the highest quality market research services. With a team of experienced researchers and analysts, we strive to deliver insightful and actionable data that helps our clients make informed decisions about their industry and market. Our customized approach allows us to tailor our research to each client's specific needs and goals, ensuring that they receive the most relevant and valuable insights.
Contact Us
Email: [email protected]
Address: 825 3rd Avenue, New York, NY, USA, 10022
Tel: UK: +44 203 695 0070, USA: +1 646 905 0080
#Network Encryption#Network Encryption Industry#Network Encryption Share#Network Encryption Size#Network Encryption Trends#Network Encryption Regional Analysis#Network Encryption Growth Rate
0 notes
Text
#Network Encryption Market#Network Encryption Market size#Network Encryption Market share#Network Encryption Market trends#Network Encryption Market analysis#Network Encryption Market forecast
0 notes
Text
before anything, please let me mention, though lebanon, same as israel, is the size of a peanut, hezbollah rules very defined regions and the attack was not ALL over lebanon, as the media likes to overdramatize. next- israel planted that in very outdated, new (pre distribution) communication devices specifically requested by nasrallah to be used by hezbollah terrorists, when israel confirmed it had breached hezbollah’s communication network months ago.
yet:
sympathizers are not worried that so many pagers purchased solely for communication purposes between people affiliated with a designated terror organization had be distributed and found a trusty owner?
a 9 year old girl was allowed near a pager used for terror purposes.
how fucking common it is to be affiliated and rank high enough to get a fucking encrypted communication device for a terror organization.
never in the history of the war against terror has there been a more precise in such a large scale attack on a terror organization, yet the antisemites still be antisemitizing.
if so many doctors got hurt, this begs the question, why did public medical personal had communication devices purchased by a terror organization in a country with a functioning government?
and most importantly: how fucking easy it is to activate the west’s white savior complex and get its pity, even when it’s absolutely ridiculous.
323 notes
·
View notes
Text
For lesbian visibility week consider boosting visibility for my (Im a trans lesbian) project to bring new, simple, cheap (mostly free), decentralized internet infrastructure to trans women, other lgbt+ people, and other marginalized people at a time when our communications are being severely cracked down on and surveilled. It's called PierMesh
You can also follow me at @utopicwork for updates
Some recent updates:
Cut packet sizes 70%
Prototype of Daisy (a distributed schemaless database) implemented
End to end encryption core nailed down
I'm hoping to get properly funded soon (we're struggling to keep ourselves afloat at the moment) so if you know someone/an organization that might fund this work please let me know
If you would like to support us financially this works best:
Otherwise there are more ways to donate on the website
Oh and one more thing, if you would like to contribute to this project Ive set up a Matrix chat for that:
Edit: fixed the invite link
331 notes
·
View notes
Text
futuristic dr | the rebel group
------------------------------------------------------------------------------
date: may 9 2025. finals are next thursday and friday. ap english exam is wednesday. sorry if this looks bad...
------------------------------------------------------------------------------



"GreyRaven? Maybe a hacker cult. Maybe corporate rebels. Maybe ghosts.”
✧˖*°࿐greyraven
GreyRaven is a decentralized vigilante syndicate operating in neovista, working outside the law to expose corruption, dismantle systemic control, and protect civilians from shadow forces like Orbis and the VEC. their name appears in encrypted messages, tagged symbols, and digital warnings across Neovista, especially when someone powerful falls.
დ࿐ ˗ˋ unit structure ✧ 𓂃 › size. 7 members ✧ 𓂃 › focus. getting rid of corruption
დ࿐ ˗ˋ selection process
✦ ˚ —initially... ✧ 𓂃 › chosen by blade. ✧ 𓂃 › now chosen by the whole team
დ࿐ ˗ˋ symbol. a sleek black raven split by a line of circuitry


დ࿐ ˗ˋ their tags.
✧ 𓂃 › a burned raven silhouette etched into metal via plasma torch. ✧ 𓂃 › a digital glitch shaped like wings that appears on Orbis or HALO system screens for 0.3 seconds before blackout. ✧ 𓂃 › a spraypainted raven eye hidden in alleyways or rooftops. ✧ 𓂃 › a shattered mirror pattern with a winged shadow inside when light reflects off glass. ✧ 𓂃 › it’s often called “The Last Shadow” by Virelia’s underground networks.



დ࿐ ˗ˋ public perception.
✧ 𓂃 › some say GreyRaven doesn’t exist. ✧ 𓂃 › others believe they’re cyber-terrorists or mythical hackers. ✧ 𓂃 › in truth, they’re the reason a dozen government black ops were leaked, and why Orbis lost a critical AI node in the Mirror District. ✧ 𓂃 › a single whisper can summon them. ✧ 𓂃 › they only appear when someone powerful is about to fall. ✧ 𓂃 › Orbis agents die with black feathers burned into their retinas. ✧ 𓂃 › HALO calls them: "unclassified threat profile ΔΣ-13"—unsolvable anomaly.
დ࿐ ˗ˋ symbols in the city.
✧ 𓂃 › when someone spots a winged glitch on a VEC drone? GreyRaven’s near. ✧ 𓂃 › when the elevators in a HALO tower fail at 3:03 a.m.? They’re climbing. ✧ 𓂃 › when an Orbis exec finds a black feather on their desk—but no one’s been in? Countdown’s begun.
დ࿐ ˗ˋ decision making.
✧ 𓂃 › all missions are proposed by Blade, validated by KT’s threat matrix, and reviewed in nightly Echelon Briefings (short, encrypted convos held within soundproofed sleep pods). ✧ 𓂃 › mist sometimes overrides plans mid-mission if AI interference is detected. no one questions her when she “feels it.”
დ࿐ ˗ˋ rules and code.
✦ ˚ — SILENCE IS SURVIVAL — No names, no recordings, no trails.
every member has multiple aliases. real names are used only inside the Nest—and only once trust is earned.
✧ 𓂃 › NO SPLIT LOYALTIES — You’re with GreyRaven, or you’re not.
divided minds get teammates killed. outside allegiances, old vendettas, or secret deals? that gets purged—fast.
✦ ˚ — EVERY SCAR TELLS A STORY — we don’t hide the pain. we weaponize it.
members are encouraged to remember their pasts, not run from them. trauma is armor—if tempered.
✧ 𓂃 › NEVER LEAVE A RAVEN BEHIND — if one falls, we all rise.
no one is abandoned. ever. rescue takes priority—even over mission success.
✦ ˚ — NO GLORY. NO GODS. NO BOSSES — we are not heroes. we are necessary.
no member is above another. blade leads, but no one follows orders blindly. question. think. act.
✧ 𓂃 › KILL ONLY WHAT KEEPS THEM IN CHAINS — revenge is poison. revolution is purpose.
death is not the goal—freedom is. if someone can be freed instead of destroyed, that’s the mission.



“They’re not a myth. They’re a mirror held to power—and sometimes, a blade at its throat.”
✧˖*°࿐members roles
დ࿐ ˗ˋ blade
ex-military turned ghost operative. went off-grid after refusing to carry out a war crime ordered by Virelia’s elite. built GreyRaven from the shadows.
✧ 𓂃 › position : tactician & close combat specialist, commander ✧ 𓂃 › signature weapon: shockwave blade (vibro-blade with EMP pulses)
დ࿐ ˗ˋ switch
a former street racer, runner, and pickpocket. survived the slums of the Dream District, where she built her own rules and fought her way out. met Blade during a riot; they’ve been inseparable since. she sees the cracks before anyone else does. did modeling too.
✧ 𓂃 › position : sniper, stealth, tech heist, recon ✧ 𓂃 › signature weapon: smartscope railgun + collapsible bow with shock-arrow mods + throw-blade set with trace disruptors.
დ࿐ ˗ˋ mist
former Orbis cybernetics prodigy. faked her death after discovering inhumane experiments on augmented children. now hacks and destroys from the inside. her body runs colder than most, with signs of experimental neural dampening. she moves like fog, disrupts like static. has a strange link to EXO.
✧ 𓂃 › position : infiltrator, tech ghost, sabotage, recon ✧ 𓂃 › signature weapon: monofilament whip + dart gun + plasma daggers with AI disruptor chips
დ࿐ ˗ˋ kt
former child hacker-for-hire turned vigilante. cracked the HALO outer firewalls at age 16. now fights AI corruption. communicates via memes mid-op. may or may not have a kill-switch on HALO’s subsystems.
✧ 𓂃 › position : cyberwarfare expert, AI counter ops, hacker ✧ 𓂃 › signature weapon: custom electro-katana + hacking gauntlet + wrist-port deck with fold-out hacking claws
დ࿐ ˗ˋ cry
once a VEC blacksite interrogator. defected after seeing too many innocent people executed as “pre-crime threats.” tracks enemies down with eerie precision. now he breaks enemies through psychology or raw data—whichever hurts more.
✧ 𓂃 › position : interrogation, close combat, heavy intel retrieval ✧ 𓂃 › signature weapon: EMP Bolas + smart gel rounds that paralyze upon contact + electrified chainblades
დ࿐ ˗ˋ J
grew up in an Orbis-owned clinic that tested cybernetic compatibility in children. escaped after killing the head researcher. now uses her knowledge to heal—or hurt. keeps her heart closed, but opens up around mist and KT.
✧ 𓂃 › position : combat medic & enforcer ✧ 𓂃 › signature weapon: reinforced gauntlets + shock-injector blade
დ࿐ ˗ˋ dawn
orphan from the 127 District’s riot zones, raised in chaos. became a transport and tactics expert. keeps the team grounded.
✧ 𓂃 › position : demolitions, vehicle tech, pilot, gear engineer ✧ 𓂃 › signature weapon: nanite grenades + smoke-gel grenades + high-velocity pistol set
⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣷⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⡇⠀⠀⠀⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣾⣿⣿⠀⠀⢸⣧⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⣀⣼⣿⣿⣿⣧⡀⢸⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠰⠶⣾⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⡶⠄⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠈⠙⢿⣿⣿⣿⡿⠋⣿⣿⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⢿⣿⡿⠀⢰⣿⣿⣷⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⠇⠀⣾⣿⢹⣿⡆⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⠀⠈⣿⢀⣼⣿⠃⠀⢻⣿⣄⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⣸⣀⣠⣿⣿⡿⠁⠀⠀⠀⠻⣿⣶⣤⡀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠠⣴⣶⣾⣿⣿⣿⣛⠁⠀⠀⠀⠀⠀⠀⠀⢙⣻⣿⣿⣷⣶⣦⡤ ⠀⠀⠀⠀⠀⠀⠀⠈⠉⣿⡟⠿⣿⣷⣦⠀⠀⠀⠀⣀⣶⣿⡿⠟⠋⠉⠉⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⢰⣿⣧⠀⠀⠙⣿⣷⡄⠀⣰⣿⡟⠁⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⣼⣿⣿⡄⠀⠀⠘⣿⣷⢰⣿⡟⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⣠⣿⣿⣿⣧⠀⠀⠀⢹⣿⣿⡿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⢀⣠⣼⣿⣿⣿⣿⣿⣷⣤⡀⠘⣿⣿⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠤⣶⣾⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⡧⠄⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠉⠙⠻⢿⣿⣿⣿⣿⣿⣿⠿⠛⠉⢹⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠈⢻⣿⣿⣿⡿⠃⠀⠀⠀⢸⡏⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⣿⣿⣿⠃⠀⠀⠀⠀⢸⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⢹⣿⣿⠀⠀⠀⠀⠀⠈⠃⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠘⣿⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⣿⠃⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⣿⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
✦ ˚ — MEMBERS OF GREYRAVEN
BLADE
SWItCH
MiST
KT
CRY
J
DAWN





"You’ll never know who we are. Only that we were here.”
✧˖*°࿐bases
bases depend on where we are during missions, as most missions last multiple days to weeks or more.
*ೃ༄the HaVen.
დ࿐ ˗ˋ central base (location: underground, U District Core)
this is the central base of operations for GreyRaven, hidden beneath an eco-engineering lab and accessed through a maintenance tunnel. the Haven acts as the heart of their operations, with a state-of-the-art holomap and surveillance systems to keep track of Neovista's ever-changing power dynamics. here, members can repair cybernetics, store weapons, and work on encrypted missions in complete secrecy. the encrypted servers and AI assistant “WRAITH” play a pivotal role in their intelligence gathering.
✧ 𓂃 › hidden beneath an eco-engineering lab. ✧ 𓂃 › accessed via an abandoned magrail maintenance tunnel.
✦ ˚ — contains. ✧ 𓂃 › holomap of Neovista with AI and surveillance bypass overlays. ✧ 𓂃 › cybernetics lab (used by KT and Ky). ✧ 𓂃 › weapons cache and stealth armor vault. ✧ 𓂃 › encrypted servers and AI assistant “WRAITH.” ✧ 𓂃 › living space for all 7 members.
✦ ˚ — visuals.

*ೃ༄the FoRge.
დ࿐ ˗ˋ black market armory (location: Dream District, rooftop-level)
this base serves as the group’s armory and testing ground for modded weapons and gear. located above a neon-lit karaoke bar, the Forge is a hidden black-market armory complete with high-tech security. blade and KT are often found here working on new weapons, including their signature Shockwave Blade and other innovative tech. it also houses a drone bay and 3D printer for custom weaponry and high-grade components.
✧ 𓂃 › high-tech security, a garage for their racing vehicles, and a command center with surveillance equipment and communication systems. ✧ 𓂃 › hidden above a neon karaoke bar. ✧ 𓂃 › Blade and KT use it to test or create modded weapons.
✦ ˚ — contains. ✧ 𓂃 › disguised drone bay. ✧ 𓂃 › 3D printer for high-grade components. ✧ 𓂃 › hardlight melee testing chamber.
✦ ˚ — visuals.

*ೃ༄the EYERIE.
დ࿐ ˗ˋ surveillance node (location: Mirror District skytower)
the Eyrie functions as a surveillance and intelligence hub, hidden in a luxury apartment tower in the Mirror District. cry and kt are in charge here, using it to hack into HALO's blind spots and intercept encrypted communications. the base includes advanced signal-bouncing tech and a system for remote camera overrides, making it an essential asset for their covert operations.
✧ 𓂃 › hidden in a top-floor garden of a luxury apartment tower, cloaked by a glass illusion and sound dampeners. ✧ 𓂃 › Cry and Kt run surveillance here.
✦ ˚ — contains. ✧ 𓂃 › live access to HALO blind spots. ✧ 𓂃 › signal bounce tech for secure calls. ✧ 𓂃 › remote camera override system.
✦ ˚ — visuals.

*ೃ༄the NEST13.
დ࿐ ˗ˋ yes (location: 127 District, apartment complex)
located in a high-floor apartment, Nest13 is an emergency hideout and staging area for their missions in the 127 District. this base is used when the group needs to stay in the heart of the city's underbelly, near their allies in the underground movement and the resistance groups. It's equipped with basic weaponry, medkits, and enough resources to support prolonged stays. like The Haven, this location provides a small, private retreat for the team when they need rest, though the facilities are more basic. the atmosphere is utilitarian, with limited comforts but ample space to plan and strategize.
✧ 𓂃 › hidden in an apartment complex above a fixers place ✧ 𓂃 › blends in as an abandoned apartment unit on the 19th floor; windows are one-way mirrored with hidden anti-drone netting.
✦ ˚ — contains. ✧ 𓂃 › DIY medbay and mechanical workbench ✧ 𓂃 › hardline access to underground rebellion networks ✧ 𓂃 › rapid-exit rappel cables woven into window frames ✧ 𓂃 › backup living quarters for low-profile periods
✦ ˚ — visuals.






"The serpent coils twice—check the mirror, not the door.”
✧˖*°࿐allies
the unlikely allies of greyraven.
დ࿐ ˗ˋ dr. veyla maren. Cybernetic Defector
once one of Orbis’s lead cybernetics researchers, Veyla defected after discovering the company was experimenting on civilians, including children, under the guise of "adaptive enhancements."
✧ 𓂃 › personality: methodical, haunted, hyper-focused. has a dry, sarcastic wit and often speaks in precise, scientific language. ✧ 𓂃 › role in GreyRaven: provides insider knowledge of Orbis tech. specializes in countermeasures, reverse engineering implants, and designing stealth augmentations.
დ࿐ ˗ˋ shadowthorn. The Whisper Broker
an elusive fixer known only through proxy channels and deepnet whispers. former hacker turned black market handler.
✧ 𓂃 › personality: paranoid, charming, unpredictable. Uses multiple voice modulators and aliases. ✧ 𓂃 › role in GreyRaven: acquires rare tech, falsified IDs, stolen military-grade equipment, and corporate data caches.
დ࿐ ˗ˋ jyNx. The Code Oracle
no one knows who JYNX is—not their face, voice, or location. Some believe they’re an AI themselves. others swear they’re a ghost in the system.
✧ 𓂃 › personality: cryptic, theatrical, obsessed with games and codes. frequently speaks in anagrams or limericks. ✧ 𓂃 › role in GreyRaven: operates the largest intel broker ring on the darkweb—BlackNet. sends out mission pings, bounty warnings, and VEC surveillance paths.
დ࿐ ˗ˋ emberline. The Bodysmith
worked in biotechnical enhancement labs before going rogue. now runs an underground clinic camouflaged as a ramen shop in the Dream District.
✧ 𓂃 › personality: stern, precise, secretly nurturing. gives off big “war medic” energy. ✧ 𓂃 › role in GreyRaven: maintains implants, removes trackers, stabilizes blood nanites, installs illegal enhancements. ✧ 𓂃 › relationship to the team: treats them like grumpy kids. thinks Blade is reckless and Switch needs more sleep. secretly keeps personal med files on each of them with affectionately grumpy nicknames.
დ࿐ ˗ˋ talon. The Fallen Commander
former VEC Peacekeeper who once led raids into Resistance districts—until he learned the truth. went AWOL with a datapad full of classified secrets.
✧ 𓂃 › personality: stoic, world-weary, a reluctant hero. speaks in clipped, tactical bursts. ✧ 𓂃 › role in GreyRaven: feeds intel on troop movements, lab locations, VEC internal disputes. knows how to exploit Peacekeeper communication systems.
დ࿐ ˗ˋ NYx. Ghost in the System
a fragmented AI consciousness from the failed EXO Sentinel project. installed into GreyRaven’s Nest network by unknown means—possibly JYNX.
✧ 𓂃 › personality: alternates between helpful and unsettling. can mimic voices. may be evolving. ✧ 𓂃 › role in GreyRaven: manages Nest’s security, stealth fielding, data processing, and reroutes all external tracing attempts. sometimes “glitches” and speaks in fragmented memories.
დ࿐ ˗ˋ rhiza. The Revolution’s Spine
grew up in the 127 District under corporate occupation. now leads a fierce rebel cell known as the Thornweavers.
✧ 𓂃 › personality: passionate, blunt, a natural firebrand. Doesn’t believe in half-measures. ✧ 𓂃 › role in GreyRaven: provides troops, weapons, and rallying influence. coordinates sabotage ops with Dawn and Switch.





“If you see a raven etched in steel or flicker on your screen—someone corrupt is about to fall.”
“Or you’re next.”
✧˖*°࿐public response
დ࿐ ˗ˋ Underground Perception.
✧ 𓂃 › to the slums and districts living under bootheels, GreyRaven are whispered like urban legends—not saviors, but avengers. ✧ 𓂃 › to the elite, they’re a growing infection. “Cyberterrorists.” “Systemic rot.” Dangerous ideologues. ✧ 𓂃 › to the youth, they’re rebellion romanticized—posters in cracked phone cases, symbols painted in alleyways like war sigils.
დ࿐ ˗ˋ Underground Art & Cultural Echoes.
✦ ˚ — “Ravens in the Ruins” murals. massive, stylized wall art appearing overnight on bombed-out buildings or blacksite walls. one of the most famous depicts a raven made of shattered glass diving into a sea of wires—signed only with "⸸".
✦ ˚ — “SLICED” (graffiti collective). anonymous, city-wide taggers whose only subjects are corruption, rebellion, and GreyRaven exploits. their tags have gone viral on the underground net: a woman made of fog beside a glitching raven, or a soldier throwing a chainblade into a corporate logo.
✦ ˚ — digital zines & qr codes. in alleyways and underpasses, QR codes printed in iridescent ink lead to:
✧ 𓂃 › pirate zines titled "WINGS OF RESISTANCE", full of GreyRaven conspiracy theory art, intercepted transmissions, and AI-glitched poetry. ✧ 𓂃 › leaked bodycam footage showing someone disabling peacekeeper drones in four seconds flat. possibly Switch.
✦ ˚ — fashion subculture. in the undercities, "Ravenwear" is its own anti-fashion statement—streetwear with torn tech fabrics, modified visors, repurposed drone parts. inspired directly by GreyRaven’s stealthwear.
დ࿐ ˗ˋ Rogue Journalism & Digital Exposure
✦ ˚ — the SHADOW feed :
✧ 𓂃 › a decentralized digital broadcast that pulses through the darkweb and flickers into hacked billboards. ✧ 𓂃 › exposes corrupt figures with evidence that mysteriously appears—voice recordings, drone footage, classified documents. ✧ 𓂃 › GreyRaven’s logo glitches into the feed briefly, and then vanishes. It’s never clear if they’re behind it—but everyone assumes.
✦ ˚ — “RAVEN’S THORN” blog :
✧ 𓂃 › a rogue journalist with heavy encryption posts exposés on Orbis, VEC blacksites, and cyberwarfare incidents. ✧ 𓂃 › the blog has a running theory: GreyRaven operates not just in Virelia—but across multiple continental nodes.
*ೃ༄☆. theories range from plausible to wild: ✧ 𓂃 › “Cry once disabled a mech suit with his voice.” ✧ 𓂃 › “Mist controls dead satellites with her mind.” ✧ 𓂃 › “KT is a failed AI that gained consciousness and grew a conscience.” ✧ 𓂃 › “Switch once vanished in a crowd of Peacekeepers and left their helmets filled with smoke.”
დ࿐ ˗ˋ "The Last Shadow" Article Series (Underground Publication)
a rogue journalist known only as "Cipher" has been releasing a series of exposé articles under the title "The Last Shadow," chronicling GreyRaven’s actions, ideology, and conflicts with corporate control. these articles are released in encrypted digital formats, often sent directly to underground data hubs or printed in small runs of pamphlets that circulate discreetly in Neovista's alternative districts.
✧ 𓂃 › the content of the articles is largely sympathetic, casting GreyRaven as vigilantes fighting against an oppressive, surveillance-heavy system. cipher's work portrays them as saviors to those who have been failed by official forces, while simultaneously cautioning readers about the price of freedom they’re offering—chaos, danger, and the destabilization of the already fragile order.
✧ 𓂃 › specialized publications, such as GlitchPoint (an underground tech journal), often publish leaked data from GreyRaven’s missions. they publish hacked corporate secrets, political manipulations, and show the true cost of corporate power in their city. the leaks often come directly from JYNX, a mysterious figure who seems to trade in secrets, and often provides cryptic advice on how to access certain hidden areas of Neovista's vast black-market network.
დ࿐ ˗ˋ Viral Coverage of GreyRaven's Operations
every major GreyRaven operation causes a viral stir in the rogue media landscape. whether it's an elaborate data hack of Orbis’ central AI node or the assassination of a corrupt corporate executive, rogue journalists covering these events in real-time often paint GreyRaven as Robin Hood figures, showing off their tactical brilliance and brutal efficiency.
✧ 𓂃 › the digital media arm of the resistance—groups like Hacktivists Unite—push the boundaries of digital freedom by sharing content that is designed to encourage public support for the syndicate. this content can range from video edits showing GreyRaven’s close combat efficiency to animated clips dramatizing their urban guerrilla tactics in symbolic, stylized ways.
✧ 𓂃 › doxxed leaks. some members of Virelia’s elite—and even powerful corporate leaders—have had their personal data released by rogue journalists. this not only jeopardizes their safety but also sends a loud message about the power and reach of GreyRaven. it's these kinds of leaks that lead to the paranoia in corporate leadership, with even the most powerful fearing the long arm of GreyRaven.
#reyaint#reality shifting#shiftblr#reality shifter#shifting#shifting community#shifting motivation#anti shifters dni#dr scrapbook#dr world#futuristic dr
12 notes
·
View notes
Text
♯ [!!!] » Acc░ss ▓rant▒d~:
"Listen—"
There's the barest quirk of her brow from under her hood — a momentary flex, involuntary, mixed with amusement and something else. Challenge perhaps. Or thrill — that familiar, stupid, addictive jolt up her spine she always got when she danced on the precipice of poking the proverbial bear and waiting to see if it would bite.
Of course, it helped that she was on one end of the wire, audio distorted, mask pulled over her nose, and traffic heavily encrypted with assumedly miles of space in between her and one on the other end.
"— it's not my fault your techs missed one firewall on their latest patch cycle. I just so happened to be in the digital neighborhood to notice."
A beat. Considering. Debating how far to push.
"But hey — that's really not bad compared to other corporate monoliths of similar size, ya know. So, don't beat them up too badly. I'm sure they just need to…” a hand raises, waves around flippantly, “… update their network documentation. Or something."
Sen7inel reclined back in her worn computer chair, sprawling lazily, her oversized hoodie a shrug from falling off one shoulder, and twirled a freshly rolled join between her fingers.
"Oh — before you worry — don't. I locked the door on my way out, free of charge — you're welcome, by the way. Not a lot going on there, seemed like a dead end. Really didn't even expect you to find my calling card, let alone that quickly."
What she didn't mention was that they would have to pay the price for the ridiculously long admin password she’d changed on the firewall to unlock that door — or hard reset it to regain access. Either way, it was a small price to pay for poor cybersec hygiene, and she'd maintain a foothold on the network to keep snooping around in the meantime.
@progenitorensis
#progenitorensis#ic;#au; re#// i debated on how to start this for a bit#// decided chaos was the only answer#// i'm down for whatever direction -- hostile or otherwise
5 notes
·
View notes
Text
Years after being accused of swinging a baseball bat at police officers during the January 6, 2021, attack on the US Capitol, Edward “Jake” Lang is now using encrypted messaging channels to create a nationwide network of armed militias in all 50 states.
Though he has been in prison for over 1,200 days, Lang is working with a network of election deniers and conspiracists to promote the North American Patriot and Liberty Militia, or Napalm for short. The group officially launched last week with 50 state-specific militia groups on Telegram.
Lang claims that the Telegram groups already have 20,000 members, including pastors, farmers, former military personnel, and currently serving sheriffs. However, multiple experts who reviewed the channels tell WIRED said that figure was wildly overestimated and that the real figure was closer to 2,500 members. But a group this size, they warn, is still large enough to cause a serious threat. And while unarmed members are welcome, the group is, at its core, a pro-gun organization. “We are pro open carry, pro always have it on you, rather than waiting for somebody else to be able to defend your life,” says Lang.
As the 2024 US election approaches, Lang says that Napalm will be focusing on potential “civil unrest” around the vote. “We have to make sure that we're prepared for any real-time scenarios, any eventualities,“ says Lang. “Civil unrest at any given moment, especially around an election time, is something that could come along, and so we have to plan for that contingency as well.”
Tensions around the November vote are already at an all-time high, and many Republicans refuse to say if they will peacefully accept the outcome of the November election. Over one-third of Americans now baselessly claim that President Joe Biden’s victory in 2020 was illegitimate. These conspiracies have led to a resurgence in far-right activity, of which Napalm is just the latest facet: Lang, along with all other members of the group’s leadership council, ardently believes that the 2020 election was stolen from former president Donald Trump.
“We've noted considerable energy being put into resurrecting far-right paramilitary activism right now,” Devin Burghart, the executive director at the Institute for Research and Education on Human Rights (IREHR), tells WIRED. “The growing talk of ‘Second Amendment remedies’ to unfavorable electoral outcomes is a serious cause for concern. Militia groups like Napalm promote political violence and sow the seeds for another potential insurrection.”
In addition to the election, Lang says that Napalm will respond to everything from natural disasters to Federal overreach, political protests, and potential Chinese invasions.
“I thought it was necessary to get organized in case these encroachments, these violations of our civil liberties, our natural rights were to escalate to a point where it'd absolutely be untenable and that we would need to defend ourselves.” Lang tells WIRED from the Metropolitan Detention Center in Brooklyn, where he is awaiting a trial set for September. “There is a tyrannical wave that has hit America that we've never seen before. And so it's time that people get organized in case they escalate to something that basically puts our very lives in danger.”
Lang, 29, is from upstate New York. He claims to have been an ecommerce entrepreneur and nightclub promoter before getting sober and finding God in late 2020. At the same time, Lang was getting deeper into “truther content” online that claimed Marxists and Communists were ruining the country. This content overlapped with election-denial conspiracies that led to the Capitol riot and inspired Lang to travel to DC.
Days after January 6, Lang was recruiting people into an armed militia on Telegram that would ostensibly fight against the incoming regime of President Biden.
“It was the first battle of the Second American Revolution—make no mistakes,” Lang wrote about the Capitol riot, according to a tranche of thousands of messages obtained by ProPublica. “This is WAR.”
That effort ended days later when Lang was arrested and charged with multiple counts of assaulting law enforcement officers, as well as felony charges of civil disorder and obstruction of an official proceeding—some of which carry a maximum sentence of 20 years in prison.
After he was arrested, Lang became a figurehead for January 6 prisoners who have been falsely portrayed as “hostages” or “warriors” by Trump and his supporters. While in prison, Lang has published a book, helped produce several films, hosted his own podcast, and raised millions of dollars for inmates and their families—all related to the January 6 attack.
“It's important to recognize that Lang is, first and foremost, a grifter who knows that his ‘political prisoner’ schtick is his only shot at relevance,” says Jon Lewis, a research fellow at George Washington University’s Program on Extremism. “This is someone who has intentionally delayed his own trial date in an effort to remain in the spotlight and who continues to promote violent conspiracies.”
And though Lang’s original attempt at starting a militia on Telegram ended with just a few hundred followers and his arrest, he says that he has spent the past year creating Napalm from his cell with the help of far-right figures from around the country.
Among those who Lang has convinced to join his initiative is QAnon promoter Ann Vandersteel, who is the groups’ national vice chairman. Former New Mexico county commissioner Couy Griffin, who is known as the leader of Cowboys for Trump, is also on the council. In 2022, Griffin refused to certify the results of a primary election vote.
Stew Peters, who will act as the militia’s national communications director, is a Florida-based antisemitic podcaster who shot to prominence in recent years by pushing Covid conspiracies, including a wild claim that Covid vaccines were derived from snake venom. The claim was so outlandish that even other conspiracy theorists dismissed his claims as “trash.” Peters has also pushed QAnon conspiracies and white supremacist content and even called for the death sentence for the “traitors” that he claimed have stolen the elections.
When the site launched last week, one of those listed as a member of the council was Richard Mack, the founder of the Constitutional Sheriffs and Peace Officers Association. When contacted by WIRED, however, Mack said he was not affiliated with the group: “Many groups contact me weekly to work together, but in order for that to happen they must join our mission and philosophy of nonviolence.”
Lang told WIRED that a member of his team had been speaking to Mack about his role with the group, and it was likely just a miscommunication. Hours later, however, Mack’s picture was removed from the website.
Guns appear to be a central aspect of all actions taken by the Napalm militias, even when responding to incidents like hurricanes, wildfires, or earthquakes. “Even in a natural disaster, people that are in desperate scenarios may do desperate things,” Lang said. “And I believe that open carry and carrying a firearm on your body is a natural right of all men, and it's not something to be shied away from.”
While Lang said non-gun-owners would be welcome to join the group: “They would still be trained, and they would definitely be supported in their eventual path to gun ownership.”
Though Lang says all militia activity to date has occurred online, Napalm plans to get into the real world soon. “We will have casual outings at local firing ranges for downrange training, different exercises on what to do if the power goes out, if the internet is shut down, if the water lines are contaminated, [and] wilderness survival training,” says Lang.
All new members have to go through a vetting process, which consists of a five-minute video call designed to weed out potential infiltration from law enforcement.
Once vetting has been completed, members are then placed in a private county-level chat group where they can communicate with other members of the militia. Neither WIRED nor the researchers we spoke to were able to gain access to the private chats.
In the past, a county-level militia cell structure has made it harder for law enforcement to infiltrate extremist groups.
Lang says the vetting process has been established in part as a response to what happened to militia groups like the Oath Keepers and Proud Boys in the wake of January 6. “They had these public group chats, and people said inflammatory things on there, and so we don't have those,” Lang said.
Though Lang claims that the group has signed up over 20,000 members, some experts don’t believe him.
“The best we can tell is that the numbers that the group is claiming are grossly misleading,” Jared Holt, senior researcher of US hate and extremist movements at the Institute for Strategic Dialogue, tells WIRED. “This is an aspirational project. It doesn't reflect any sort of organizing infrastructure that's actively been built. It is being promoted by a group of political hucksters and shock jocks. And I wouldn't be surprised if would-be joiners of these groups come to learn that there is some kind of membership fee, some sort of financial component involved here.”
Burghart and his colleagues at IREHR also reviewed the 50 state-level Telegram channels and found a total of just over 14,000 members. However, Burghart also says that he believes that this figure is “significantly artificially inflated, with real membership closer to 2,500.”
Lang did not respond to questions about whether the Telegram channels membership numbers were artificially inflated.
But even with inflated membership numbers and lack of real-world coordination so far, experts still believe attention needs to be paid to groups like Napalm.
“The promotion of this kind of rhetoric and just mobilizing people around this idea could have reverberating effects,” says Holt. “It certainly heightens the tension of the political environment. It could certainly drive individuals who are maybe suffering some sort of crisis into thinking about more violent action or taking more extreme measures in their anti-government worldviews. And even if one of these states materializes into something with a dozen people in it, that could still cause a real problem.”
16 notes
·
View notes
Text
From the beginning | Previously | Coin standings | 60/70 | 39/39
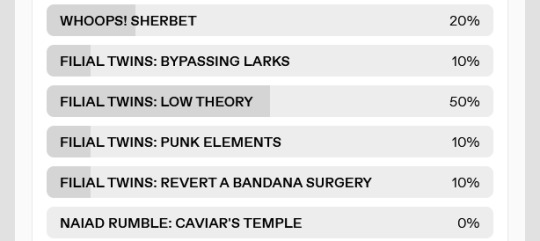
You decide to double up and head to the holy tower, where you might find more gifts waiting for you from the butterfly cloud. And while you're there, you can install the WIFI ACCESS POINT up in the governor's office and take a look at some files.

Nothing crazy happening this time! You're just gonna get a menu of shop items and a slate of hallucinations.
Hey, here they come now!
BIONIC MINTER (40)
RELINER STAFF (30)
HACK IN NIL (22)
OW, PANIC! ICE FISTS! (12)
A COUCH FÉVER (10)
BILATERAL SIZINGS (9)
A SNARE WORM (3)
NOBLE BELT TUT (2)
STOPWATCH FARE (2)
BEAT USER (1)
The FILIAL TWINS go ahead and INSTALL WIFI for you, and you've got a backdoor right into the governor's private network! Spicy. The files in there, though... are tough to make heads or tails of. There's...
A medal awarded to something- whatever it is, IT PREVENTED ROOK POWER EXTRUSION by stopping someone or something from juicing chess pieces for magical strength.
Some juice, which contains a tiny molecule that's way more regal than the other juice molecules. Plus it's a lady molecule, who's in charge. Hurry! ACCESS QUEENLIEST JUICE ION, PRONTO!
A tiny robot body is doing some sort of alchemy. TIN RUNT COCOCTS A QUART O' CACTI, which is one of the harder-to-drink beverages available. Spiky.
The guy writing this fanfic squirts you with a little mister bottle, like you use for produce. Hey! SPRITZ? REPENT, WRY ED COOLHAXX! But I'll never repent. Sorry, not sorry.
Cleanliness is next to godliness, but what's next to molasses? To find out, we're asking God. Join in on this NEXT TO MOLASSES SACRAMENT and you too can learn the secrets of the universe!
(These files are long and dense and well-encrypted! The top two poll options will be explored for next update's base hunger spend.)
Continued | 60/70 | 37/37
#lost in hearts#re: speculation in the notes of last update: not *everything* in datasouls proper is an anagram#but maybe i should make them be for consistency's sake#shackle of ignorance doesn't decrypt to anything iirc but i should come up with something#rejected poll title: FRIGHTEN POOH'S SOUL. good but risks offending Disney or Xi Jinping
14 notes
·
View notes
Text
IoT Security Challenges in India: Protecting Smart Homes & Connected Devices

IoT is transforming the way people live by making their homes smart with devices such as security cameras, smart locks, and voice assistants. In India, IoT technology is adopted at a pace that cyber threats are rising rapidly. With weak security protocols, outdated software, and unawareness, Indian households are vulnerable to cyberattacks. In this blog, we will explore the major IoT security challenges in India and how individuals can safeguard their smart homes and connected devices. If you are looking to strengthen your understanding of cybersecurity, enrolling in a cyber security course can be a game-changer.
The IoT Boom in India
India is witnessing the highest adoption of IoT across homes and businesses. From smart TVs to intelligent thermostats, IoT is revolutionizing life. This booming technology, however, offers a large target size for hackers too who exploit the vulnerability of devices to gain unauthorized access to data.
Fundamental Drivers of IoT Adoption in India:
Increased internet penetration with low-priced data plans
Government initiatives such as Smart Cities Mission and Digital India
Increasing adoption of smart home devices as they become increasingly affordable
Growing application of industrial IoT in health, agriculture, and manufacturing
Chief IoT Security Challenges in India
Poor Authentication & Default Passwords
Most IoT devices have a factory-set password that the user ignores or fails to change. Hackers exploit these default credentials to take over the devices, entry private networks, and crack sensitive information.
Lack of Security Updates & Patches
Most smart devices have limited or no firmware updates, which makes them vulnerable to cyber threats. Many Indian consumers do not check for security updates, leaving their devices susceptible to known exploits.
Data Privacy Concerns
Smart devices collect vast amounts of personal data, from voice recordings to daily routines. Without stringent data protection policies, this information can be misused or leaked by malicious actors.
Botnet Attacks & DDoS Threats
Cybercriminals hijack unprotected IoT devices to form botnets, which are used to launch massive Distributed Denial of Service (DDoS) attacks. These attacks can cripple networks and cause disruptions to online services.
Unsecured Wi-Fi Networks
Many Indian households rely on poorly secured Wi-Fi connections, providing an easy entry point for hackers. Without encryption or strong passwords, attackers can intercept sensitive information and compromise connected devices.
Absence of Specific Cybersecurity Legislation for IoT
India has advanced in data protection with the Digital Personal Data Protection Act, but there is no dedicated IoT security framework. The absence of it leaves the manufacturer to choose cost over security and sell devices which are not so well protected in the market.
How to Secure Smart Homes & Connected Devices
Change Default Credentials
Always change the default usernames and passwords of the IoT after installation. Use strong, unique passwords and implement multi-factor authentication wherever possible.
Update Firmware Periodically
Scan for software and security updates on all smart devices, and install them as soon as they are available. In case your device can no longer get any updates, consider replacing it with a newer version that is at least as secure.
Secure Your Wi-Fi Network
Use a robust Wi-Fi password, and make sure WPA3 encryption is turned on. Limit remote access to your router, and make an IoT-specific network so that those devices can't contaminate your primary network.
Firewall & Security Solutions The use of firewalls and network security solutions monitors traffic and can block malicious activity on IoT networks. 5. Limit Data Sharing & Permissions
Assess permission for smart appliances and reduce or limit the devices from accessing unsecured personal information. De-activate unused add-ons, remote access in devices.
Cyber Security Courses
IoT-based cyber-attacks are minimized if awareness against the threat builds. To boost that awareness further, take time out to become a certified graduate of cyber security by signing for courses in areas like best security practices, principles of ethical hacking, and defending digital systems.
Road Ahead to Improving Indian IoT Security:
The Indian government, device manufacturers, and consumers must take proactive steps to mitigate IoT security risks. Stronger security standards, public awareness, and robust cybersecurity laws are the need of the hour to secure the future of IoT in India.
Conclusion
IoT devices offer incredible convenience but also introduce significant security risks. Protecting smart homes and connected devices requires a combination of best practices, awareness, and robust cybersecurity measures. By staying informed and adopting the right security strategies, individuals can ensure a safer IoT experience.
If you’re passionate about cybersecurity and want to build expertise in protecting digital systems, consider taking a cyber security course to gain hands-on knowledge and skills in ethical hacking, network security, and data protection.
3 notes
·
View notes
Text
I've been thinking more about this robot ABO idea i've had. Infodump time!!!!!!
So. Here, alphas, betas and omegas are (obviously) robots. They are all different, highly advanced machine models, designed for symbiotic cooperation and replication by a long lost race of creators. Much like biological beings, their prime objective is to spread, adapt and simply survive in the universe.
There are basic 3 models of this robot, each complenting other models with its unique capabilities and fulfilling a different function in the bigger picture.
Alphas are the "basic" unit, specializing in protection, labor and leadership. They are sturdy, versatile units designed for a wide range of difficult tasks from mining to outer space operations however they usually cannot do much more than just surviving without support from betas and repairs from omegas
Omegas are the caretakers, responsible for replication, repairs and construction. They are less tough and slightly smaller than alphas, but are the only model capable of producing more units and repairing them. They usually perform complex tasks, such as logistics, engineering or sciences, but are virtually helpless without alphas and betas.
Betas are a bit tricky. Instead of one unit, a single beta is actually a highly modular, tiny machine which joins together with other betas to form a collective consciousness and become a single beta. Kinda like a nanomachine. While they can work standalone, similarily to alphas, betas were designed to serve a supporting role by using their ability to shapeshift to provide alphas and omegas with tools needed to perform specific tasks, such as mining equipment, shielding, weapons, computational power etc. Their unique role results in betas frequently forming long-lasting, professional bonds with other models.
There is also a 4th, temporary model. Its a young robot, freshly assembled by a omega. Its described below.
Instead of packs, they form "networks", which function alike to their organic counterparts. A network is usually being managed by an alpha with the help of their omega, as a commune of many units typically attached to some specific place and a task. Thus, instead of being governed by a central authority, their species is fractured into innumerable networks scattered around the cosmos, some made only of a few units on a remote planet, some made of billions of units on a planet sized gigapolis.
Ofcourse, they would also have their own mating practices. Once an omega deems the conditions appropriate, it would search for a secure place to enter nesting mode. Its body would transform into a immobile, egg-like form and broadcast an encrypted signal with its location in hopes of attracting a suitable partner. If they are capable enough to decrypt it and get the omegas location, it would venture to the omega to mate. Once together, the two models would connect and begin exchanging data needed for the omega to begin assembling offspring.
Omega would stay like this for a few weeks, during which it would construct a new robot inside their body. This "pup" would be a unique, temporary model that would over time be upgraded by the omega and eventually by itself. Upon reaching maturity it would go into a "puberty" phase and transform its young form into a full alpha, beta or an omega.
#alpha beta omega#abo#abo headcanons#robot abo#omegaverse#omegaverse headcanons#robots#robot omegaverse#non standard
2 notes
·
View notes
Text
Top Cybersecurity Solutions Providers in Delhi-NCR: Wish Geeks Techserve
Cybersecurity services in India have become an essential investment for businesses looking to safeguard their digital infrastructure from rising cyber threats. With an increasing number of data breaches, phishing attacks, and malware infiltrations, organizations cannot afford to overlook the importance of strong IT security frameworks. Companies in Delhi-NCR, in particular, need to prioritize security due to the region's rapid technological growth and evolving cyber risk landscape.
Finding the top cybersecurity solutions provider in India is crucial for ensuring business continuity, regulatory compliance, and data integrity. Among the top contenders offering robust security solutions is Wish Geeks Techserve, a trusted IT security services India provider known for its innovative and customized cybersecurity strategies.
The Growing Cybersecurity Challenges in India
As the digital economy expands, businesses face a multitude of security threats ranging from ransomware attacks to sophisticated hacking attempts. The emergence of remote working models and cloud computing has further increased the vulnerability of organizations, making network security services in India a necessity rather than an option. The cyber threat landscape includes:
Phishing and Social Engineering Attacks: Cybercriminals exploit human vulnerabilities through fraudulent emails and deceptive practices to gain unauthorized access to sensitive information.
Malware and Ransomware Infections: Malicious software infiltrates systems, encrypting or corrupting critical business data, often leading to significant financial losses.
Insider Threats and Human Errors: Employees, either maliciously or unintentionally, can cause security breaches through weak passwords, mishandling of data, or lack of security awareness.
DDoS (Distributed Denial-of-Service) Attacks: Hackers overwhelm business networks with excessive traffic, leading to downtime and operational disruptions.
Cloud Security Risks: With increasing cloud adoption, businesses must ensure secure cloud storage, access management and data encryption practices to prevent unauthorized intrusions.
Why Choose Wish Geeks Techserve as the Best Cybersecurity Company in India?
Wish Geeks Techserve stands out among cybersecurity solutions providers in India, offering state-of-the-art security services tailored to businesses of all sizes. Their comprehensive approach ensures complete protection from internal and external threats. Here’s what makes them the ideal IT security services India provider:
1. Advanced Cybersecurity Solutions for End-to-End Protection
Wish Geeks Techserve provides holistic security solutions that cover all aspects of IT security. Their expertise spans across:
Threat Intelligence & Risk Assessment: Proactively identify vulnerabilities and strengthen weak points before attacks occur.
Endpoint Protection & Malware Defense: Implementing security measures that shield endpoints like computers, mobile devices and IoT systems from cyber threats.
Firewall & Intrusion Prevention Systems (IPS): Ensuring that network boundaries remain impervious to unauthorized access attempts.
Incident Response & Forensics: Swift action in the event of a cyberattack, minimizing damage and preventing future breaches.
2. Comprehensive Network Security Services in India
As a leading cybersecurity solutions provider in India, Wish Geeks Techserve specializes in network security services in India, ensuring robust defense mechanisms against cyber threats. Their network security offerings include:
Secure VPN Implementations: Allowing safe and encrypted remote access for employees working from different locations.
DDoS Protection & Mitigation: Preventing large-scale cyberattacks that aim to disrupt operations.
Zero Trust Security Frameworks: Adopting a ‘never trust, always verify’ approach to user authentication and access control.
3. 24/7 Cybersecurity Monitoring & Incident Response
Cyber threats do not operate within business hours, which is why Wish Geeks Techserve provides round-the-clock monitoring and support. Their dedicated Security Operations Center (SOC) continuously tracks anomalies, preventing attacks before they escalate.
4. Regulatory Compliance & Data Privacy Solutions
With stringent data protection regulations like GDPR and India’s upcoming Personal Data Protection Bill, businesses must comply with legal security mandates. Wish Geeks Techserve helps companies meet these requirements by implementing industry-leading compliance strategies and ensuring secure handling of customer and business data.
5. Customized Cybersecurity Strategies for Businesses
Recognizing that no two businesses have the same security needs, Wish Geeks Techserve delivers customized cybersecurity services in India based on industry-specific challenges. Whether it's securing financial transactions, protecting healthcare records, or preventing e-commerce fraud, their team crafts personalized solutions to fit organizational requirements.
How Businesses Can Benefit from Strong Cybersecurity Measures
Adopting best-in-class IT security services India offers multiple benefits beyond just data protection. Businesses that invest in top-tier security measures experience:
Improved Customer Trust: Demonstrating commitment to data privacy enhances brand credibility.
Reduced Financial Losses: Preventing cyberattacks reduces the risk of hefty ransom payments, fines and revenue losses due to downtime.
Operational Efficiency: Secure IT environments enable seamless business operations without disruptions from malware or unauthorized access.
Competitive Advantage: Businesses that prioritize cybersecurity gain an edge over competitors who fail to implement robust security strategies.
Conclusion
Cybersecurity is no longer a choice but a necessity for businesses in Delhi-NCR and across India. Choosing the right cybersecurity solutions provider in India can make all the difference in ensuring business continuity and protection against cyber threats. Wish Geeks Techserve emerges as one of the best cybersecurity companies in India, offering cutting-edge IT security services in India that cater to businesses of all sizes. Their expertise in network security services in India ensures that organizations remain resilient against evolving cyber risks.
If you’re looking for a trusted partner to fortify your cybersecurity infrastructure, Wish Geeks Techserve is the go-to provider, ensuring that your business stays secure in the ever-changing digital landscape. Invest in strong security measures today and safeguard your business’s future!
#Best Cybersecurity Company in India#IT Security Services India#Cybersecurity Solutions Provider in India#Network Security Services in India
4 notes
·
View notes
Text
Sims 4 house -a high standard decoration modern mansion

Modern & Minimalist & Fashionable

The 1307 Sierra Mansion is a modern luxury home with a unified style of ceiling decoration(The first person perspective of the ceiling is visible,and the third person perspective is not blocking the view), building materials, furniture, and decorative items specially crafted.
The vast majority of building materials, furniture, and decorative items in houses are meticulously modeled and tuned.They are both textured and fully functional, and are placed in the perfect position of the house,creating a modern spatial design that is very beautiful, exquisite, and fashionable.

Housing configuration

House Features:
Will not prompt for lost furniture items, what you see is what you get.
The exterior and interior decoration of the building are quite modern and fashionable, with textured furniture and specially designed ceilings. The first person perspective is visible, while the third person perspective is not.
The entire house has almost no overlapping objects putting, causing flickering of object textures.
The second floor of the building has two flowing water features. If a simulated citizen passes through this area, they will Walk on stone slabs, which will not create a strange water walking scene,and so on.
The interaction of furniture functions is very complete and will not block simulated citizens, resulting in inability to interact.
Almost anywhere you go to the house, you won't get stuck.
The elevator lobby can be conveniently and quickly moved between the third floor, saving a lot of time.
The basketball court theme can be modified in construction mode, providing 30 themes.
The vast majority of furniture has storage and placement function, and hangers can hang clothes.
Basketball Court
More styles

The floor texture, walls, and ceiling treatment here are excellent, and the lighting design has a sense of layering, creating a good sports atmosphere.
The house offers 30 basketball court themes that can be customized in construction mode.
Take A Look
More HD images of the house

Usage Information
Game version
Your game needs to be version 1.77.131.1030 or higher.
Packs
The house uses the following combination packages to ensure the integrity of the decoration effect.

For Windows only
This house only supports Windows systems.The usage of this house is the same as using a house in daily gaming, with a Mods folder and a Tray folder, it just the cc files of this house has been encrypted, and once unlocked with one click using the files unlocking tool, the house can be used.
House file size
1.87GB
Lot
64 x 64, recommended for placement inWindenburg
Download
Because the house file is a little large, so the house is stored in TearBox, which is a network disk service for free,using TearBox to achieve extremely fast downloads.
click here to download the whole house
Download
House Video
Here are my two YouTube videos of the house , one about the design of the space and one about simulating people interacting with the house.
youtube
youtube

#thesims4#sims4house#sims4housebuild#sims4cc#sims4ccfinds#sims4#sims4mods#sims4mansion#sims4modernhouse#sims4building#ts4#ts4cc#ts4 mods#Youtube#ts4 house
23 notes
·
View notes
Text
Essential Cybersecurity Measures for Organizational Network Protection

In today's interconnected world, a robust cybersecurity strategy is no longer a luxury, but a necessity for organizations of all sizes. A strong defense against ever-evolving cyber threats is paramount to protecting sensitive data, maintaining business continuity, and preserving reputation. This blog explores critical cybersecurity organizational network protection measures.
Understanding the Threat Landscape
Before diving into protective measures, it's crucial to understand the threats organizations face. These include:
Malware: Viruses, ransomware, and spyware designed to damage or steal data.
Phishing: Deceptive emails or messages tricking individuals into revealing sensitive information.
Denial-of-Service (DoS) Attacks: Overwhelming networks with traffic, disrupting services.
Insider Threats: Malicious or accidental actions by employees or other insiders.
Data Breaches: Unauthorized access and exfiltration of sensitive data.
Essential Cybersecurity Measures
A layered approach is key to effective network protection. Here are some crucial measures:
Firewall Implementation: Firewalls act as a barrier between your network and the outside world, controlling incoming and outgoing traffic based on predefined rules. Regularly updating firewall rules is critical.
Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activity, alerting administrators to potential threats and even automatically blocking malicious traffic.
Antivirus and Anti-malware Software: Deploying robust antivirus and anti-malware software on all endpoints (computers, servers, mobile devices) is essential to detect and remove malicious software. Regular updates are crucial.
Strong Password Policies and Multi-Factor Authentication (MFA): Enforcing strong, unique passwords and implementing MFA adds an extra layer of security, making it significantly harder for attackers to gain access even if a password is compromised.
Regular Security Audits and Vulnerability Assessments: Regularly assessing your network for vulnerabilities and conducting security audits helps identify weaknesses before they can be exploited.
Employee Training and Awareness: Human error is a major factor in many security breaches. Regular cybersecurity awareness training for all employees is vital. This training should cover topics like phishing awareness, password security, and safe browsing practices.
Data Encryption: Encrypting sensitive data, both in transit and at rest, protects it even if a breach occurs.
Regular Backups and Disaster Recovery Planning: Regularly backing up critical data and having a disaster recovery plan in place ensures that you can recover from a cyberattack or other disaster.
Network Segmentation: Dividing your network into smaller, isolated segments limits the impact of a breach. If one segment is compromised, the others remain protected.
Incident Response Plan: Having a well-defined incident response plan in place allows you to react quickly and effectively to a security incident, minimizing damage and downtime.
Building a Cybersecurity Culture
Effective cybersecurity is not just about technology; it's also about people and processes. Building a strong cybersecurity culture within your organization is crucial. This involves:
Leadership Buy-in: Securing support from top management is essential for allocating resources and prioritizing cybersecurity.
Open Communication: Encouraging employees to report suspicious activity without fear of reprisal.
Continuous Improvement: Regularly reviewing and updating your cybersecurity policies and procedures to stay ahead of evolving threats.
Xaltius Academy's Cybersecurity Course: Your Partner in Network Protection
Navigating the complex world of cybersecurity can be challenging. Xaltius Academy's cybersecurity course provides comprehensive training and equips you with the knowledge and skills needed to protect your organization's network. Our expert instructors and hands-on labs will prepare you to effectively implement and manage these critical security measures. Invest in your cybersecurity future and safeguard your organization's valuable assets.
Conclusion
Protecting your organization's network requires a proactive and multi-faceted approach. By implementing these essential cybersecurity measures and fostering a strong security culture, you can significantly reduce your risk of falling victim to cyberattacks and safeguard your organization's future.
2 notes
·
View notes
Text

Growing into the Job, Post 373: Evolution Concerns
We’re just worried that her growth chart is beginning to look logarithmic came the message, the most recent in a series of alarmist communiques from a technician at their daughter company in the US.
Kristina Zhestakova had received the first text as she’d been talking with prospective recruits, young women in their second and third year. She was now between meetings, walking down the hallways of The Medical University of Warsaw. The school was her alma mater and she recognized most of the landmarks, the twists and turns of the old passages, the labs and classrooms. Many of the professors were new; the plaques on the office doors had been largely replaced by female names. Twenty years, she thought with a nod, had brought on some welcome changes.
You are working on the sequencing data? she replied, relying on the translation software of KOLECTV’s encrypted messaging app. Her English had improved over the last couple decades, ever since she’d been tasked with establishing the company’s first North American facility on the island off Mexico's coast, but she still preferred writing in her native Polish. She was glad this technician - Marcia was her name - used the secure proprietary messenger as she’d been asked; not all at this upstart American company Evolution Pharmaceuticals did.
Yes we have the bloodwork. Working on it but it’s complicated, came the tech's next message. They all knew that MM-1A’s eldritch origins complicated things, making the polymerase chain reactions difficult and keeping them from using the Sanger or NGS. The witches and their ways tended to do that, make everything either too easy or too much of a chore. But KOLECTV’s science had learned and become powerful. We’ve already identified the location of the breath and the voice.
Yes. Doctor Zhestakova’s heels <click-click-clicked> on the tiled hallways of the medical school. Ostensibly, she was still, in title, Senior Vice President of Biotechnology at Gray Global Enterprises, once an American shipping empire that was now little more than a shell company for a good-sized group of the collective’s holdings. KOLECTV, technically, was one of those. However, in the early days, like a tick it had drained GGE’s resources and quickly came to dwarf its parent company and now controlled its interests. It was now an enormous, if still shadowy, network with tendrils not only in the medical and scientific industries around the world, but deep in other businesses, banking and politics.
The hope was that, soon - especially after the victorious results in the recent American elections - KOLECTV would finally shed the false auspices of GGE and begin to reveal itself. It would grow in power tenfold, it knew, when it could step out of the shadows on its six-inch stilettos and begin to claim its empire. When it is done send the sequencing package to my team at Coronado.
Of course Doctor. We’ve also located multiple other newly active gene loci, of unknown phenotype expression, the technician’s next message explained. Dr. Zhestakova knew what that meant, other potential abilities budding within the subject.
She’d spent many of her early years with the company, after being sent to America soon after medical school for project “Bridesmaid”, and then setting up and studying at their island research facility, KOLECTV’s first in the New World. The project, nearly twenty years prior to today, had ultimately resulted in the takeover of GGE and the facility was now one of many jewels in the crown of the movement. Dr. Zhestakova had been not only an operative (088) in that operation and an integral player in building the prototypes for what the women of the new world could be, but an early beneficiary subject (Program, 3133j) as well.
Send it all. But tell no one else, for now. I want Coronado to go over it so we can develop an isolation plan. Dr. Zhestakova knew that Oksana and others in KOLECTV’s higher ranks were made nervous by her tendencies towards self-autonomy and transgression; she’d seen the old files they kept on her. She knew that her independent streak, coupled with her Program-gifted intelligence and with what they called her “relative lack of empathy” was seen as both a powerful opportunity for the movement but something they struggled to keep in check. She knew her file also described her tendencies for excessive behaviors and indulgences. Those, over the past decade or so, she’d made good progress in controlling, reining in.
She could really use some vodka.
The height? The explosion in strength? We’re not worried? came the technician’s concern..
Fuck the height and strength. I’ve seen the monsters they’d made, the failed experiments in Siberia and Kazakhstan. That can be dealt with when the time comes. Let the other abilities manifest first, so we learn, glean, farm. No we are not yet concerned.
Others would be, she knew. Others would be very concerned. Dr. Zhestakova could only do so much, but she had been trying her best to keep the snowballing irregularities in Project MM-1A's case “under the radar”, as they might say in the US. If they were to attract notice, the project could get shut down; Kristina knew there was so much potential to be culled, so much that could be achieved. Just imagine, she found herself thinking, an army of superwomen not only bigger, taller, stronger than any man alive, like we’d planned…
No, the possibilities might go well beyond that.
…but impervious to heat, and harm, and bullets…
And in a rare moment of heart-pounding speculation…
Imagine an army of women that can fly…
=========================================
for more on the enigmatic, psychopathic and high-functioning alcoholic Dr. Zhestakova, as well as “Project Bridesmaid”, please see required reading “Trophy”
19 notes
·
View notes
Text
Top 5 Must-Have Features for a Successful eCommerce Website
In today’s digital era, creating a successful eCommerce website requires much more than just displaying products। The features that guarantee a smooth shopping experience, such as easy navigation and secure transactions, are essential for a profitable online store। These are the top five must-have features for a successful eCommerce website, whether you’re launching a new one or updating an existing one। Visit Us: http://www.shanviatech.com
1. User-Friendly Navigation
Customers may leave a congested website before they get a chance to look around. Navigating the various sections of your store with ease requires user-friendly navigation. Users should be able to readily locate categories, items, and information on the website thanks to its intuitive structure and well-organized menu. Important components of intuitive navigation consist of:
· Search Bar: A robust search functionality that allows users to find products using keywords, categories, or product codes.
· Categories and Filters: Properly organized product categories and filters (price, size, color, etc.) help customers narrow down their choices.
· Breadcrumbs: Provide users with a clear path to navigate back to previous pages without confusion.
Good navigation ensures that customers spend less time looking for what they need, resulting in higher satisfaction and increased conversions.
2. Mobile Responsiveness
By 2024, mobile eCommerce will still be quite popular as so many consumers will be shopping and browsing on smartphones. In order to take advantage of this enormous market, your eCommerce website needs to be mobile-friendly. With a responsive design, your website will adjust to various screen sizes with ease, offering the best possible viewing experience across desktop, tablet, and mobile devices. Among the main advantages of mobile responsiveness are:
· Improved User Experience: A mobile-friendly website is easier to navigate and increases customer engagement.
· SEO Benefits: Search engines like Google prioritize mobile-responsive websites, improving your site’s search rankings.
· Higher Conversion Rates: With more users shopping via mobile, a responsive design leads to higher sales and customer retention.
In addition to annoying visitors, a non-responsive website lowers its exposure in search results, which can seriously harm your company.
3. Secure Payment Gateways
One of the most important features of an eCommerce website is security. Consumers must feel secure when transacting, particularly in light of the growing worry over online fraud and data breaches. Gaining a customer’s trust requires integrating a secure payment gateway. To guarantee secure transactions, the following components are essential:
· SSL Encryption: Secure Socket Layer (SSL) encryption protects sensitive information, like credit card details, during the checkout process.
· Multiple Payment Options: Offer various payment methods, including credit cards, debit cards, digital wallets (e.g., PayPal, Apple Pay), and even buy-now-pay-later options to cater to a diverse audience.
· PCI Compliance: Ensure your website complies with the Payment Card Industry Data Security Standards (PCI DSS) to protect customers’ payment data.
In addition to increasing trust, a secure checkout procedure lowers cart abandonment, which boosts revenue and fosters client loyalty.
4. Fast Loading Speed
Conversion rates and user experience are closely related to website speed. Customers become irritated and may quit a website that loads slowly before completing a purchase. In fact, studies reveal that a little one-second lag in page load speed can cause a 7% decline in conversions. Important techniques to enhance loading speed consist of:
· Optimized Images: Compressing images without losing quality can drastically improve page load times.
· Content Delivery Network (CDN): A CDN distributes content across multiple servers worldwide, ensuring faster delivery of web pages.
· Minimized Code: Reducing unnecessary code, including HTML, CSS, and JavaScript, ensures quicker page rendering.
Not only does a quick website keep users interested, but it also helps you rank higher in search results because Google values site speed highly.
5. Customer Reviews and Testimonials
In the field of eCommerce, customer reviews are an invaluable resource. They encourage potential buyers to feel confident about the quality of products, which acts as social proof and influences their purchasing decisions. A mechanism that makes it simple for customers to post reviews and read those of others should be included in any successful eCommerce website. Key characteristics include of:
· Verified Reviews: Ensure that only verified buyers can leave reviews, which builds trust in the authenticity of feedback.
· Star Ratings and Comments: A combination of star ratings and written reviews gives customers detailed insights into a product’s performance.
· Review Moderation: Implement a moderation system to prevent spam or fake reviews from appearing on the site.
Testimonials and reviews that are positive increase trustworthiness, encourage conversions, and have a big effect on customer retention.
User experience, security, and functionality must be given top priority on your website if you want to compete in the fiercely competitive eCommerce market. Building trust, interacting with clients, and increasing sales all depend on features like user-friendly navigation, responsiveness on mobile devices, safe payment gateways, quick loading times, and customer reviews. You’ll not only create a seamless buying experience by adding these essential elements, but you’ll also grow your online business to unprecedented levels.
Visit Us: http://www.shanviatech.com
3 notes
·
View notes
Text
A Comprehensive Guide to Blockchain-as-a-Service (BaaS) for Businesses
In today's digital landscape, a blockchain app development company plays a crucial role in transforming industries with decentralisation, immutability, and transparency. However, building and managing a private blockchain network can be complex and costly, which deters many businesses. Blockchain-as-a-Service (BaaS) simplifies this by allowing businesses to leverage blockchain without the challenges of infrastructure development.
This comprehensive blog covers the hurdles businesses face when adopting blockchain, how BaaS can bridge these gaps, and why it is a game-changer for various sectors.
I. Challenges for Businesses in Blockchain Adoption
Despite the undeniable potential of blockchain technology, businesses face several significant challenges when contemplating its adoption:
Limited Internal Expertise: Developing and maintaining a private blockchain network requires a skilled team with deep blockchain knowledge, which is often lacking in many organisations.
High Cost: The infrastructure investment and ongoing maintenance fees associated with blockchain can strain budgets, especially for small and medium-sized businesses (SMBs).
Integration Complexities: Integrating a blockchain network with existing enterprise systems can be challenging, requiring seamless data flow and compatibility between the blockchain system and legacy infrastructure.
II. Understanding BaaS and Its Operational Fundamentals
Blockchain-as-a-Service (BaaS) simplifies the development and deployment of blockchain applications by providing a cloud-based platform managed by third-party providers. The BaaS market, valued at $1.5 billion in 2024, is projected to grow to $3.37 billion by 2029, reflecting a robust 17.5% CAGR.
Key Components of BaaS
Cloud-Based Infrastructure: Ready-to-use blockchain infrastructure hosted in the cloud, eliminating the need for businesses to set up and maintain their networks.
Development Tools and APIs: Access to a suite of tools and APIs to create and deploy blockchain applications quickly.
Platform Support: Compatibility with various blockchain protocols such as Ethereum, Hyperledger Fabric, and Corda, offering flexibility to businesses.
Managed Service Model: Providers handle tasks like network maintenance, security updates, and scalability.
Pay-as-you-go Pricing Model: Reduces upfront investment and operational costs associated with blockchain software development.
III. Business Benefits of Blockchain as a Service
Adopting BaaS offers numerous advantages, including:
Enhanced Scalability: Businesses can easily scale their blockchain network as their needs grow.
Increased Efficiency: Eliminates intermediaries and streamlines transactions, improving productivity.
Enhanced Transparency: Tamper-proof records of transactions foster trust and improve auditability.
Reduced Costs: The pay-as-you-go model eliminates large upfront investments.
Improved Security: Built on secure cloud infrastructure with robust encryption protocols.
Enhanced Customer Engagement: Facilitates secure and transparent interactions with customers, building trust and loyalty.
IV. Industry-wise Key Use Cases of Blockchain as a Service
BaaS is transforming business operations across various industries:
Finance: Streamlines trade finance, secures cross-border payments, and enhances KYC and AML compliance.
Supply Chain Management: Improves transparency and traceability of goods, automates logistics processes, and reduces counterfeiting risks.
Healthcare: Facilitates secure sharing of patient data and tracks the provenance of pharmaceuticals.
Government: Enhances transparency with secure citizen identity management and verifiable voting systems.
V. Region-wise Adoption of BaaS
The BaaS market is experiencing rapid growth worldwide:
North America: Leading with over 35% of global revenues, driven by early adoption.
Europe: Countries like Germany, the UK, and France are at the forefront.
Asia-Pacific: China, India, Japan, and South Korea are key contributors.
Rest of the World: Growing adoption in South & Central America, the Middle East, and Africa.
VI. Why Choose a Prominent BaaS Provider?
Opting for a blockchain app development company that offers BaaS can significantly impact the success of your blockchain initiatives:
Specialised Expertise: Providers possess in-depth knowledge and experience in blockchain technology.
Cost Efficiency: Eliminates the need for in-house infrastructure investment and maintenance.
Time Savings: Accelerates the development process and reduces time-to-market.
Scalability and Flexibility: Offers scalable solutions that can adapt to business growth.
Risk Mitigation: Providers handle security, maintenance, and updates.
Conclusion
By adopting Blockchain-as-a-Service (BaaS), businesses can simplify blockchain integration and focus on innovation without the complexities of managing infrastructure. Systango, a leading blockchain app development company, offers tailored BaaS solutions that help businesses leverage blockchain technology for enhanced efficiency, scalability, and security. As one of the top , Systango also excels in integrating AI solutions to drive business growth and efficiency.
Original Source - https://systango.medium.com/a-comprehensive-guide-to-blockchain-as-a-service-baas-for-businesses-5c621cf0fd2f
2 notes
·
View notes